Key Takeaways
- Shor's algorithm threatens Bitcoin's ECDSA signatures; Grover's algorithm poses minimal risk to SHA-256 mining due to difficulty adjustment
- Breaking Bitcoin requires approximately 2,330 logical qubits; current systems have ~100 physical qubits and zero reliable logical qubits for cryptographic attacks
- Expert consensus places the earliest viable quantum attack between 2028 and 2033 with 20-60% probability depending on window
- Approximately 25-33% of Bitcoin supply (5-7 million BTC including Satoshi's coins) has exposed public keys vulnerable to future quantum harvest
- BIP-360 proposes three-phase migration: soft fork introducing P2QRH outputs, hard fork freezing legacy signatures, and optional recovery mechanism
Every few months the same headline reappears: "Google's New Quantum Chip Threatens Bitcoin." IBM announces a roadmap milestone. Media outlets declare cryptocurrency obsolete. Then nothing happens. The gap between quantum computing headlines and quantum computing reality remains vast. Understanding that gap requires distinguishing between two numbers most articles confuse: physical qubits and logical qubits.
Google's Willow chip operates with 105 physical qubits. Breaking Bitcoin's signature scheme requires approximately 2,330 logical qubits. These are not the same measurement. Current quantum computers possess zero reliable logical qubits capable of running cryptographic attacks. The threat is real but distant. Bitcoin has time to upgrade, and developers already draft the migration plan.
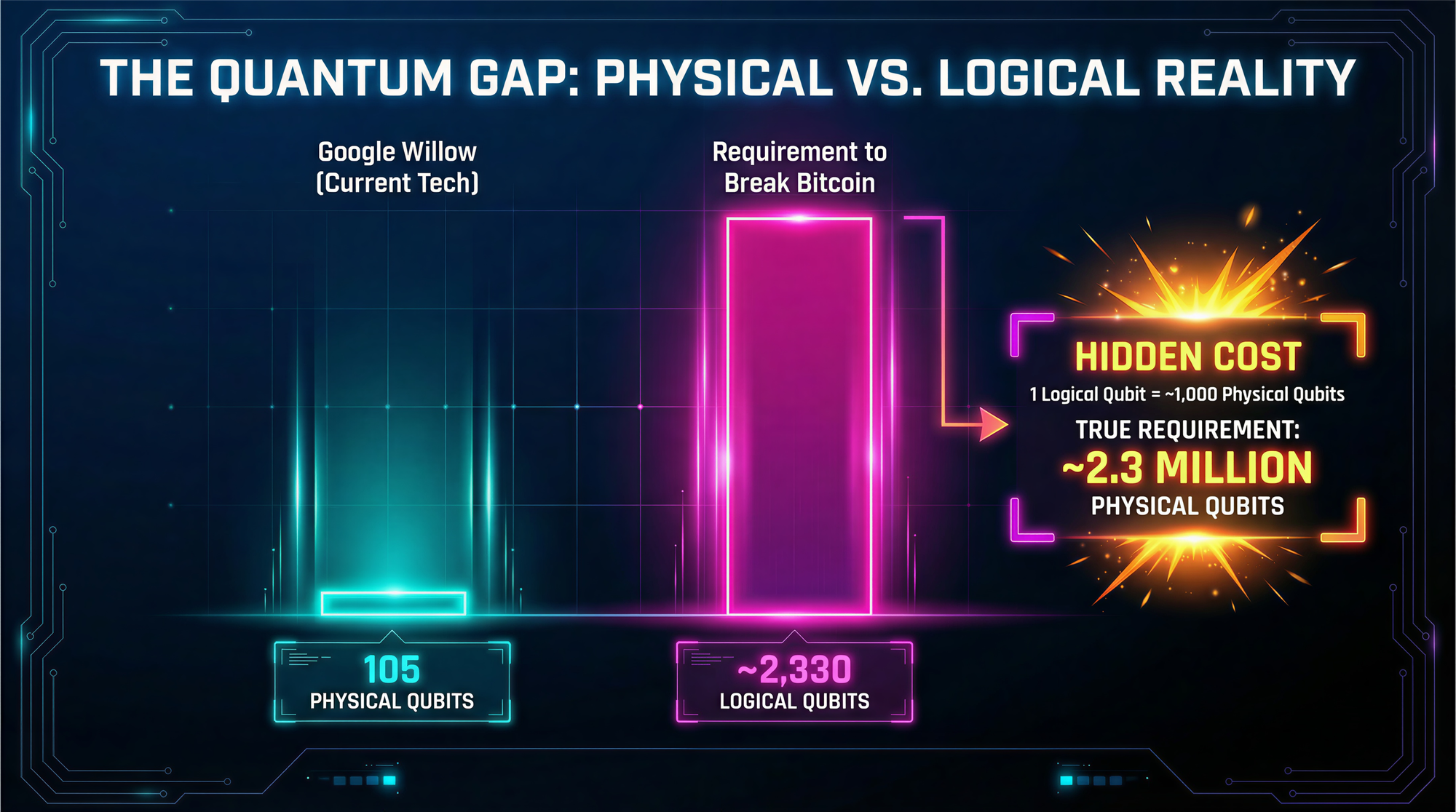
Physical Qubits vs Logical Qubits: The Number Everyone Gets Wrong
Quantum computers suffer from noise. Physical qubits degrade, lose coherence, and produce errors at rates that make sustained computation impossible. Fault-tolerant quantum computing solves this through error correction: encoding many physical qubits into single logical qubits that resist noise.
The ratio between physical and logical qubits depends on error rates. Surface codes at current error rates (approximately 0.1%) require 1,000 physical qubits per logical qubit. Newer qLDPC codes promise 12 to 14 times better efficiency. Even with optimistic assumptions, breaking Bitcoin demands between 100,000 and 10 million physical qubits.
Google Willow demonstrated 105 physical qubits with a distance-7 surface code in late 2024. The chip achieved 0.143% logical error per cycle. This represents genuine progress in error suppression. It does not represent progress toward breaking cryptography. IBM's roadmap targets 200 logical qubits by 2029 and 2,000 by 2033. Neither milestone exists today.
When headlines claim quantum computers threaten Bitcoin, ask one question: physical or logical? The answer reveals whether the threat is real or speculative.
The Threat Model: What "Breaking Bitcoin" Actually Means
"Breaking Bitcoin" encompasses several distinct attacks with different feasibility levels. Conflating them produces confusion. The primary threat targets digital signatures. The secondary threat targets hash functions. Only one matters in the near term.
Shor's Algorithm: The Existential Threat to ECDSA
Bitcoin transactions require digital signatures proving ownership. The network uses ECDSA on the secp256k1 elliptic curve. Every signature derives from a private key. Every private key corresponds to a public key. The security assumption: deriving private keys from public keys is computationally infeasible for classical computers.
Shor's algorithm breaks this assumption. It solves the elliptic curve discrete logarithm problem in polynomial time. Given a public key and a sufficiently powerful quantum computer, an attacker recovers the private key and forges transactions.
The resource requirements are precise. Research by Roetteler et al. (2017) establishes the baseline:
Logical qubits required: 9n + 2⌈log₂(n)⌉ + 10
For Bitcoin's 256-bit curve: 9(256) + 2(8) + 10 = 2,330 logical qubits
Toffoli gate count: approximately 1.26 × 10¹¹ gates (126 billion)
Runtime estimates vary based on assumptions. Conservative projections (Webber et al. 2022) suggest 317 million physical qubits for a one-hour attack. Optimistic projections incorporating 2024 algorithmic improvements suggest 100,000 to 1 million physical qubits for attacks spanning hours to weeks.
The key insight: physical qubit requirements dropped from 20 million (2019 estimates) to roughly 1 million (2024 estimates) due to improved circuit algorithms and better error correction codes. Progress is real. The threshold remains far.
Grover's Algorithm: Why Bitcoin Mining Remains Safe
Grover's algorithm threatens hash functions rather than signatures. It provides quadratic speedup on unstructured search problems. For Bitcoin mining and SHA-256, this reduces effective security from 256-bit to 128-bit.
The math: classical brute force requires 2²⁵⁶ operations. Grover's algorithm requires √(2²⁵⁶) = 2¹²⁸ operations.
This sounds catastrophic until you calculate 2¹²⁸. That number equals approximately 3.4 × 10³⁸ operations. Even with quantum speedup, finding SHA-256 preimages remains computationally astronomical. Hash-based security retains enormous margins.
Mining faces additional practical barriers. Bitcoin's difficulty adjustment recalibrates every 2,016 blocks (approximately two weeks). If a quantum miner appears with superior hashrate, network difficulty increases to compensate. The attacker's advantage evaporates within the adjustment window.
Building a fault-tolerant quantum computer costs billions in research and infrastructure. Gaining two weeks of elevated mining revenue before difficulty adjustment does not justify that investment. Grover-based mining attacks are economically irrational.
The timeline hierarchy: Shor's algorithm threatens signatures first. Grover's algorithm threatens mining only 10 to 20 years after signatures become vulnerable.
The "Satoshi" Vulnerability: Which Coins Face Risk?
Shor's algorithm requires the attacker to possess the target's public key. Bitcoin's address formats determine when public keys become visible. This distinction separates vulnerable coins from protected ones.
P2PK: Permanently Exposed Keys
Pay-to-Public-Key (P2PK) outputs store the full public key in the scriptPubKey field. The key sits visible on the blockchain from the moment of creation. Attackers need not wait for spending activity.
Approximately 1.77 million BTC remain in unspent P2PK outputs. This includes Satoshi Nakamoto's estimated 1 million BTC. These coins date to Bitcoin's first years when P2PK was standard. Many belong to lost wallets with no remaining private key holder.
P2PK addresses face immediate risk once cryptographically relevant quantum computers emerge. Attackers can compute at leisure. No time pressure exists.
P2PKH and SegWit: Revealed Upon Spending
Pay-to-Public-Key-Hash outputs store a hash of the public key rather than the key itself. The public key reveals only when the owner spends funds by including it in the transaction's scriptSig.
Classical computers cannot reverse RIPEMD-160 hashes to recover public keys. Grover's algorithm reduces this security from 160-bit to 80-bit (2⁸⁰ operations). That remains infeasible: approximately 10²⁴ quantum operations.
The vulnerability emerges at broadcast time. When a P2PKH transaction enters the mempool, the public key becomes visible. An attacker with an operational quantum computer could theoretically derive the private key before miners confirm the transaction. Typical confirmation takes 10 minutes for one block. Even optimistic Shor runtime estimates span 9 hours to one week. In-flight attacks appear unlikely.
The real risk: address reuse. Users who receive funds at the same address multiple times expose their public key after the first spend. Subsequent deposits remain vulnerable indefinitely.
Taproot: The Safest Current Option
Taproot key-path spending never reveals the public key on-chain. Only script-path spending exposes keys. For users seeking maximum quantum resistance within current Bitcoin, Taproot addresses (bc1p...) offer the best protection.
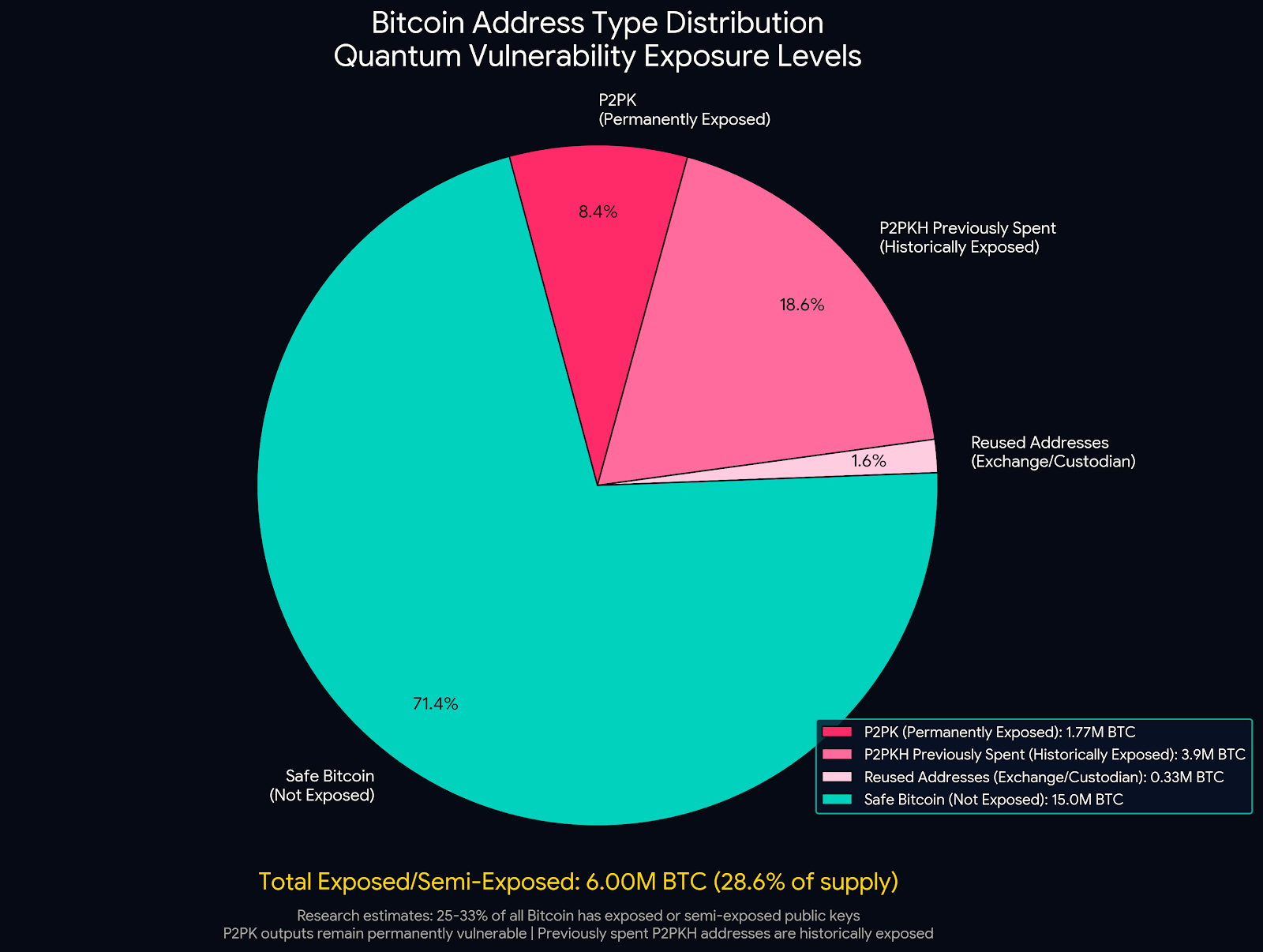
Quantifying Exposure
Research estimates 25% to 33% of all Bitcoin (5 to 7 million BTC) has exposed or semi-exposed public keys:
- 1.77 million BTC in P2PK outputs (permanently exposed)
- 3.9 million BTC in previously spent P2PKH addresses (historically exposed)
- Unknown amounts in reused addresses across exchanges and custodians
Harvest Now, Decrypt Later: The Silent Threat
Adversaries need not wait for quantum computers to begin attacks. The "harvest now, decrypt later" strategy involves collecting exposed public keys today for future decryption.
Every P2PK output displays its public key. Every spent P2PKH transaction reveals its key in the blockchain's permanent record. Nation-states, intelligence agencies, and sophisticated actors can compile databases of exposed keys. When quantum computers mature, they decrypt at scale.
This strategy makes the threat timeline more urgent than hardware announcements suggest. Data collection requires no quantum capability. Only the final decryption step depends on future technology. Coins with exposed keys face backdated vulnerability.
The implication for holders: moving coins to fresh Taproot addresses provides protection even if quantum computers arrive sooner than expected. Keys that never appear on-chain cannot be harvested.
Timeline: When Does Risk Become Material?
Expert consensus surveys and hardware roadmaps converge on a window. The probability distribution matters more than point estimates.
Current State (Late 2025)
| Milestone | Date | Details |
|---|---|---|
| Google Willow | Dec 2024 | 105 physical qubits; distance-7 surface code; 0.143% logical error per cycle |
| QuEra demonstration | Nov 2024 | 48 logical qubits (neutral atoms) |
| IBM Quantum Starling (roadmap) | 2029 | 200 logical qubits; 100M error-corrected operations |
| IBM Blue Jay (roadmap) | 2033 | 2,000 logical qubits; 1B gate circuits |
Google Willow represents a milestone in error correction rather than cryptographic threat. The chip demonstrated that adding physical qubits can reduce logical error rates (error suppression factor of 2.14 per distance increase). Previous systems showed the opposite trend. This proves fault-tolerant quantum computing is achievable. It does not prove it is imminent.
Probability Estimates by Window
| Timeline | Probability | Reasoning |
|---|---|---|
| 2025-2027 | <5% | Current hardware at ~1,000 physical qubits; no credible path to CRQC |
| 2028-2030 | 20-40% | IBM Starling roadmap; earliest credible window opens |
| 2030-2033 | 40-60% | IBM Blue Jay target; most expert consensus favors this window |
| 2033-2040 | 80%+ | High likelihood given sustained progress |
These estimates assume continued hardware progress without fundamental physics barriers. They assume no covert quantum development programs operating ahead of public disclosure. They assume no major algorithmic breakthroughs accelerating or delaying timelines.
What Could Accelerate the Threat
Several factors could compress timelines:
- Error correction breakthroughs: qLDPC codes reduce physical-to-logical ratios dramatically
- Algorithm improvements: Better circuit designs for scalar multiplication continue emerging
- Classified programs: Nation-state quantum efforts operate without public disclosure
What Could Delay the Threat
Several factors could extend timelines:
- Decoherence barriers: Scaling physical qubits while maintaining coherence may prove harder than projected
- Engineering bottlenecks: Cryogenic systems and control electronics face practical limits
- Funding constraints: Quantum research requires sustained multi-billion-dollar investment
The Solution: BIP-360 and Post-Quantum Migration
Bitcoin can upgrade its cryptography. The protocol has changed before through soft and hard forks. Developers already propose migration frameworks. The question is coordination rather than capability.
BIP-360: A Three-Phase Migration Plan
BIP-360 (Lopp et al., July 2025) outlines a phased transition to quantum-resistant cryptography.
Phase A (Soft Fork): Introduce Post-Quantum Outputs
Timeline estimate: ~2028 earliest activation
Miners begin enforcing new P2QRH (pay-to-quantum-resistant-hash) output types. Users migrate funds voluntarily over approximately three years. Old nodes continue seeing a valid blockchain. Non-disruptive transition begins.
Phase B (Hard Fork): Freeze Legacy Signatures
Timeline estimate: ~2030-2031
All ECDSA and Schnorr signatures become consensus-invalid. Bitcoin not migrated to post-quantum addresses becomes permanently unspendable. Creates hard deadline forcing migration. Economically disruptive for unmigrated holdings.
Phase C (Optional Hard Fork): Recovery Mechanism
Timeline estimate: Post-Phase B if needed
Allows recovery of unmigrated funds through zero-knowledge proof of BIP-39 seed possession. Prevents permanent loss. Adds implementation complexity.
Post-Quantum Signature Schemes: The Tradeoffs
NIST finalized three post-quantum standards in August 2024. None matches ECDSA's compact 64-byte signatures. Bitcoin throughput decreases regardless of choice.
ML-DSA (Dilithium): The Likely Consensus Choice
- Type: Lattice-based (Learning With Errors problem)
- Key size: ~1.3 KB
- Signature size: ~2.4 KB (approximately 34× ECDSA)
- Verification: Fast
- Status: FIPS 204 standardized
- Advantage: NIST standardization provides institutional confidence; well-analyzed security assumptions
ML-DSA emerges as the probable consensus choice for Bitcoin adoption. Its NIST standardization means extensive cryptanalysis and regulatory acceptance. Implementation libraries exist across programming languages.
FALCON: The Size-Efficient Alternative
- Type: Lattice-based (NTRU)
- Signature size: ~690 bytes (approximately 15× ECDSA)
- Verification: Moderate speed
- Status: NIST finalist; late 2024 finalization expected
- Advantage: Smallest post-quantum signatures
- Disadvantage: Harder to implement correctly; requires precise floating-point arithmetic
FALCON offers better scalability for Bitcoin's block size constraints. Its smaller signatures mean less throughput reduction. Implementation complexity makes bugs more likely.
SLH-DSA (SPHINCS+): The Conservative Backup
- Type: Hash-based (stateless)
- Signature size: ~17 KB (approximately 164× ECDSA)
- Verification: Slow
- Status: FIPS 205 standardized
- Advantage: Security relies only on hash function properties (well-understood)
- Disadvantage: Signature size devastates Bitcoin throughput
SLH-DSA serves as a fallback if lattice-based cryptography faces unexpected breakthroughs. Its hash-only security assumptions are more conservative. Its size makes primary adoption impractical.
Throughput Impact
| Scheme | Signature Size | Throughput Impact | Security Basis |
|---|---|---|---|
| ECDSA (current) | 64 bytes | ~7 TPS baseline | Elliptic curves |
| FALCON | ~690 bytes | ~5-6 TPS | NTRU lattices |
| ML-DSA | ~2.4 KB | ~2-3 TPS | LWE lattices |
| SLH-DSA | ~17 KB | <1 TPS | Hash functions |
Bitcoin's transaction throughput decreases by 50% to 85% depending on scheme selection. Layer 2 solutions (Lightning Network) and batching become more important.
Decision Framework: Assessing Your Quantum Exposure
Use these questions to evaluate your position and determine necessary actions.
Do You Hold Coins in P2PK Outputs?
P2PK addresses display public keys permanently on-chain. Check your wallet for addresses starting with "1" from Bitcoin's early years. If you control P2PK outputs, move them to Taproot addresses immediately. This eliminates permanent exposure regardless of quantum timeline.
Do You Reuse Addresses?
Address reuse exposes your public key after the first spend. Each subsequent deposit to that address increases attack surface when quantum computers arrive. Generate fresh addresses for every transaction. Modern wallets automate this through HD derivation.
What Address Format Do You Use?
Address formats carry different exposure profiles:
- P2PK (rare, legacy): Immediate risk; migrate now
- P2PKH (addresses starting with "1"): Risk after first spend; migrate to Taproot
- P2SH (addresses starting with "3"): Depends on underlying script; evaluate individually
- P2WPKH (addresses starting with "bc1q"): Risk after first spend; consider Taproot migration
- P2TR (addresses starting with "bc1p"): Lowest current risk; key-path spending never exposes keys
Is Your Holding Timeline Beyond 2030?
Long-term holders face higher cumulative exposure as quantum timelines approach. Begin transitioning to Taproot addresses now. Follow Bitcoin Core development discussions for protocol upgrade announcements.
Do You Use a Hardware Wallet?
Hardware wallets require firmware upgrades to support post-quantum signature schemes. When BIP-360 or similar proposals activate, your device needs updated cryptographic libraries. Verify your manufacturer commits to long-term firmware support. Budget for potential hardware replacement if devices cannot be upgraded.
Institutional Considerations
Exchanges and custodians often reuse addresses for operational efficiency. Large cold storage wallets concentrate billions of dollars on single keys. Institutional holders should audit address reuse practices and plan migration infrastructure before protocol-level enforcement.
Counterarguments and Rebuttals
"Quantum Computing Is Always 10 Years Away"
This skepticism held validity in 2015. Progress from 2020 to 2025 is undeniable. Google's error correction breakthroughs and IBM's detailed roadmaps represent engineering milestones rather than theoretical promises. Expert surveys now favor 2028-2033 rather than "decades away." Dismissing the threat is unfounded.
"Bitcoin Will Adapt Faster Than Quantum Scales"
Partial truth. Bitcoin can migrate to post-quantum cryptography. Doing so requires hard consensus across developers, miners, node operators, exchanges, wallet providers, and users. SegWit activation took approximately two years despite broad agreement on its benefits. BIP-360 involves more disruptive changes. Bitcoin's social layer moves slower than quantum hardware progress.
"Hash Protection Secures Addresses Until Spending"
Only partially true. P2PKH addresses gain hash protection until the first spend. Address reuse eliminates this protection for subsequent deposits. P2PK addresses have no hash protection at all. The ~25% of Bitcoin with exposed keys refutes claims of universal hash security.
"No One Would Build a Quantum Computer Just to Steal Bitcoin"
True for mining attacks. False for signature theft. A nation-state or large corporation might justify ~$1-10 billion in quantum development costs for:
- Intelligence gathering (monitoring cryptocurrency flows)
- Economic disruption (causing Bitcoin market crash)
- Direct profit (~$500 billion in potentially vulnerable BTC)
Mining reward theft is economically irrational. Dormant address theft at scale is not.
The Simple Mining Angle
Quantum computing does not threaten mining operations today. Grover's algorithm offers no practical advantage at current or projected technology levels. Your ASIC hashrate remains secure.
What matters is operational resilience across long time horizons. Simple Mining's hosting infrastructure operates with institutional-grade security and precision billing based on actual power consumption. Our Cedar Falls facility houses North America's largest ASIC repair center with on-site technicians. Machines stay operational instead of shipping across the country for maintenance.
We provide approximately 65% renewable energy mix across 150+ MW of U.S.-based capacity. Precision metering ensures you pay for measured consumption rather than estimates. Our team monitors protocol developments and positions clients for transitions as Bitcoin evolves.
Whether that evolution includes post-quantum cryptographic upgrades or efficiency improvements, operational infrastructure matters more than speculative threats. Sound operations compound returns. Headline anxiety does not.
Conclusion
Quantum computers will break Bitcoin's current signature scheme. The math is certain. The timeline stretches to 2028 at earliest. Bitcoin's developers already design the upgrade path. The threat is real, quantifiable, and manageable.
Ready to build productive Bitcoin exposure while the protocol evolves? Shop our bitcoin mining machines and secure hashrate backed by operational infrastructure designed for the long term.
